Contact us: info@tenendo.com
Understanding Social Engineering:
Social engineering is a manipulative technique used by cybercriminals to deceive individuals into divulging confidential information or performing actions that compromise security.
Unlike traditional hacking methods that rely solely on technical vulnerabilities, social engineering exploits human psychology, trust, and behaviour.
Examples include phishing emails that mimic legitimate organisations, pretexting where attackers fabricate scenarios to extract information, or baiting that lures victims into downloading malicious software.
Understanding social engineering is crucial because, despite advancements in technology, humans remain the weakest link in cybersecurity.
By raising awareness, implementing training programs, and fostering a culture of scepticism, organisations can mitigate the risks associated with social engineering attacks and safeguard sensitive information and assets.
Typical social engineering attack chain
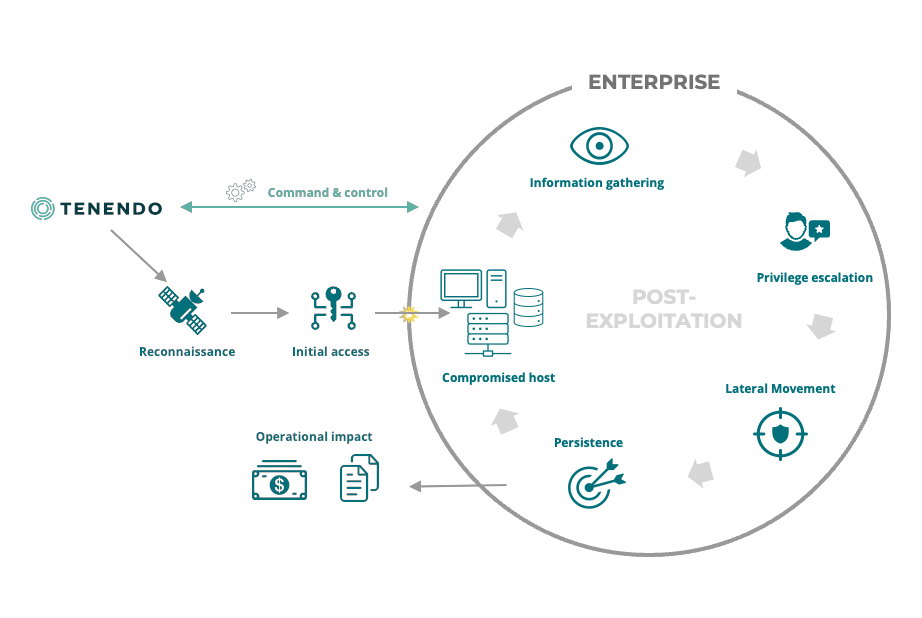
- Reconnaissance: Attackers gather information about the target, including identifying potential victims, their roles, organisational structures, and communication patterns.
- Preparation: Using the information collected, attackers prepare customised messages or scenarios, ensuring they appear legitimate and convincing to the intended victims.
- Engagement: Attackers initiate contact with the victim through various channels such as emails, phone calls, or social media. This phase often involves creating a sense of urgency, fear, or curiosity to prompt a response.
- Exploitation: Once engaged, the attackers leverage psychological manipulation techniques to deceive the victim. This could involve impersonating a trusted individual, creating a faux sense of familiarity, or using authority to coerce action.
- Action: With the victim’s trust gained, the attackers persuade them to disclose sensitive information, transfer funds, click on malicious links, or download malware-infected files.
- Exfiltration: After successfully obtaining the desired information or compromising the target system, attackers remove traces of their presence, making it challenging to detect the breach immediately.
Social Engineering Approaches and Tactics
Social engineering attacks utilise a variety of approaches and tactics designed to exploit human behaviour and manipulate victims. Here are some common approaches and tactics employed in social engineering attacks:
- Phishing: Attackers send deceptive emails, messages, or websites that mimic legitimate entities, enticing victims to provide sensitive information such as passwords, credit card details, or login credentials.
- Pretexting: The attacker creates a fabricated scenario or pretext to gain the victim’s trust. This might involve impersonating a trusted individual, like an IT support technician, to request access credentials or personal details.
- Baiting: Attackers lure victims by offering something enticing, such as free software downloads, gift cards, or promotional offers. The bait is designed to persuade victims to click on malicious links or download malware-infected files.
- Tailgating/ Piggybacking: In physical security contexts, attackers exploit courtesy or a lack of vigilance by following authorised personnel into restricted areas without proper authentication.
- Quid Pro Quo: Attackers offer a service or benefit in exchange for information or access. For instance, posing as a consultant offering technical support and requesting login credentials or system access in return.
- Watering Hole Attack: Attackers compromise a legitimate website frequented by the target group, infecting it with malware. When users visit the site, their systems become infected, allowing attackers to gain access to their networks or data.
- Impersonation: Attackers pose as someone the victim trusts, such as a colleague, bank representative, or service provider, to extract sensitive information or initiate unauthorized transactions.
- Fear or Intimidation: Using scare tactics, attackers create a sense of urgency or fear, pressuring victims to act quickly without verifying the authenticity of requests. This might involve threats of legal action, account suspension, or other consequences.
Recognising these approaches and tactics is crucial for individuals and organisations to adopt effective countermeasures, such as security awareness training, multi-factor authentication, and strict verification protocols, to defend against social engineering attacks.
